About The Devices On wobla My Network Component
Content
Learn how to identify and match the device mac address shown in the Home Network Security app with the mac address on the device. In some situations, particularly apartments, devices sometimes linger on the connect line and wait for that easy connection to sneak onto the network. Find the default gateway IP addressfor your network connection. Open Command Prompt and execute the tracert command. However, even devices you don’t recognize may be something you own that you didn’t remember.
- Wi-Fi or a wireless data connection is required to re-activate your iPhone after a reset.
- Check if you can find out the current connections to your router with a netstat-like command.
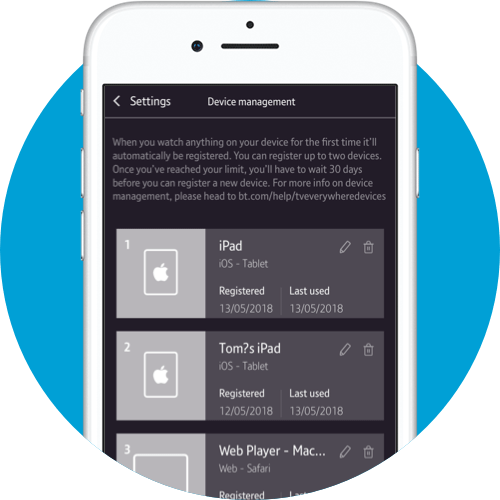
- After the scan, you can see an overview of the discovered devices and their hardware information on the All Devices page.
- In most of the cases, the wifi intruders are the neighbors or mostly your neighbor kids.
- As such, Belarc Advisor demonstrates some of these enterprise management capabilities by performing a network device discovery.
In 1950, Nielsen then moved to television, developing a rating system using the methods he and his company had developed for radio. That method became the primary wobla source of audience measurement information in the US television industry. In September 2020, Nielsen started compiling a weekly Top 10 list of most-watched shows on streaming platforms.
How To Identify Unknown Devices Connected To Your Network
Simply upload, email, or link the captures files and get the results. It helps to resolve network issues faster and flawlessly. Besides, it includes features such as drag-and-drop capture files, drop-box-like activity, allows sharing of links with co-workers, and offers advanced analysis. Only looking into the standards.ieee.org/develop/regauth/oui/oui.txt list helped to find out that the unknown devices on my network were our Motorola Mobility phones. Among SolarWinds powerful tools, the IP Address Manager does everything a large-scale enterprise needs to manage its addresses properly.
Services
Sometime those tools are capable to recognize at least brand of device. Aruba automated routine network management tasks like device discovery in Aruba Central. Smaller companies without security infrastructure can still implement this approach by procuring communication services that are inherently secure. “Buy device encryption and management from your carrier,” he said, “and insist that their mobile communication service filters for malware.” In this case, rogue AP discovery is just one of many things that your WLAN does for you. An embedded WIPS will spot more devices, faster, than you could ever hope to spot with periodic scans.
We will cover some easy ways to track all the devices connected to your wireless network. It can happen because several people might have access to your wireless network. Enter your router’s admin password and tap the LOGIN button. The devices that are connected to your router display.
View And Manage Device Connections
This works in most cases, where the issue is originated due to a system corruption. You can download Restoro by clicking the Download button below. Some routers will not have an option of disabling WPS while others lack this feature (they are probably more secure and won’t bring up rogue devices on your computer). You will no longer be able to see potential devices.
Wireless Network Watcher For Windows Only
Connect your device to a Wi-Fi network, or make sure it has a strong Verizon wireless network connection. SolarWinds Network Performance Monitor and Response Time Viewer for Wireshark are professional tools and work amazingly. They can not only identify and troubleshoot network issues in real-time but also perform multiple tasks simultaneously, such as display essential data, calculate network response time, and more. These tools increase the depth of the network analysis efforts dramatically. Cloudshark is a platform designed to display network capture files directly in the browser without the need for desktop applications or tools.
Your Home Network
Internet searches didn’t bring anything back that was useful. It seems anything with a web interface that doesn’t want to use port 80 seems to opt for port 8888 as a fallback. So the next logical step was to try to connect to that port using a browser. Note that we’re not providing nmap with an IP range. We’re focussing nmap on a single IP address, which is the IP address of the device in question.
Controlling which mobile devices can connect to your network is crucial to ensuring the privacy and integrity of corporate assets and data. Despite this, virtually every network audit uncovers at least a few surprise nodes, ranging from printers and wireless APs to mobile devices carried by visitors, suppliers and employees. If you have set a simple password for your home Wi-Fi network, other people might be able to use it.
The background scan interval can be set from the Advanced Options window . WiFi technology is everywhere these days and it seems almost every electronic device around has a wireless network connection of some sort. Laptops, tablets, smartphones, digital cameras, printers, gaming consoles, smart home devices, and many other things can connect to each other or the internet through a WiFi connection. A wireless network setup also presents its own set of problems when it comes to your own home network and the devices attached to it. Additionally, Nmap is a network scanner that’s been around for a while.







